Secure software in concept, source code and development processes
Software development is a complex topic. There are numerous programming languages, frameworks, design patterns, methods and practices. Where there are many possibilities, there are also many opportunities for errors and security deficits. As a rule, the development projects also focus on functional enhancements; security is rarely a selling point.
Exploiting vulnerabilities in software is a common tool in cyberattacks and poses a threat to software vendors and users alike. Once exploited, vulnerabilities can be used to generate unauthorised access and data breaches, spread malware, compromise internal company networks or carry out denial-of-service attacks.
We offer you various services to provide you, as the owner of a software product, with an overview of the vulnerability of your product or the resilience of your development and operating processes.
Our software security services at a glance:
Security Design & Architecture Review
Conceptual analysis of security design and architecture
We analyse design decisions and the architecture of your software product for vulnerabilities that could be abused by an attacker. This applies to modern architectures based on micro services from hyperscalers such as Microsoft Azure as well as to classic client-server applications. We gain an overview by analysing input documents (e.g. architecture diagrams, flowcharts, component diagrams or other technical documentation) and by interviewing the responsible (lead) developers.
Your bonus
In a joint dialogue, we identify deficits and potential for improvement in the security design and architecture of your software product.
For a comprehensive analysis and the greatest possible added value, a combined implementation of the security design & architecture review is recommended
- Config check: Review of the implementation of secure design and architecture approaches when configuring the application platform
- Source code security review (see below): Checking the implementation of secure design and architecture approaches during the development of the software product
Source Code Security Review
Static technical analysis of the source code – white box testing
Good design and a resilient software architecture are important cornerstones. Ultimately, what matters when it comes to the security of a software product is the clean and technically secure implementation of security aspects in the source code. We analyse the source code of your product using market-leading Static Application Security Testing (SAST) tools automatically and/or by eye and manually.
Your bonus
We identify security deficits directly in the source code of your product. Thanks to our in-depth insight into the source code, we can provide you with far-reaching certainty about the security status quo. The findings are also discussed with the responsible lead developers.
Penetration Test
Dynamic technical analysis of the software product – grey and black box testing
The functions of your software product are tested by Swiss Infosec AG penetration testers from an offensive perspective. We usually operate using the grey box method, whereby we receive valid accounts from you with which we can also examine the application in an authenticated manner. Swiss Infosec AG generally follows the best practices of the Open Web Application Security Project (OWASP) when carrying out these penetration tests. See also
- OWASP Web Security Testing Guide (WSTG)
- OWASP Top 10 Web Application Security Risks
- OWASP API Security Project
- OWASP Mobile Top 10 | OWASP Foundation
See for more information about penetration tests
DevSecOps Review
Review of the DevSecOps pipeline and associated processes
Appropriate processes and the use of modern tools and settings in development, deployment and operations can ensure that the security of software products is maintained in the long term. Together with the responsible lead developers of your software product, we examine the handling of security over the entire lifecycle.
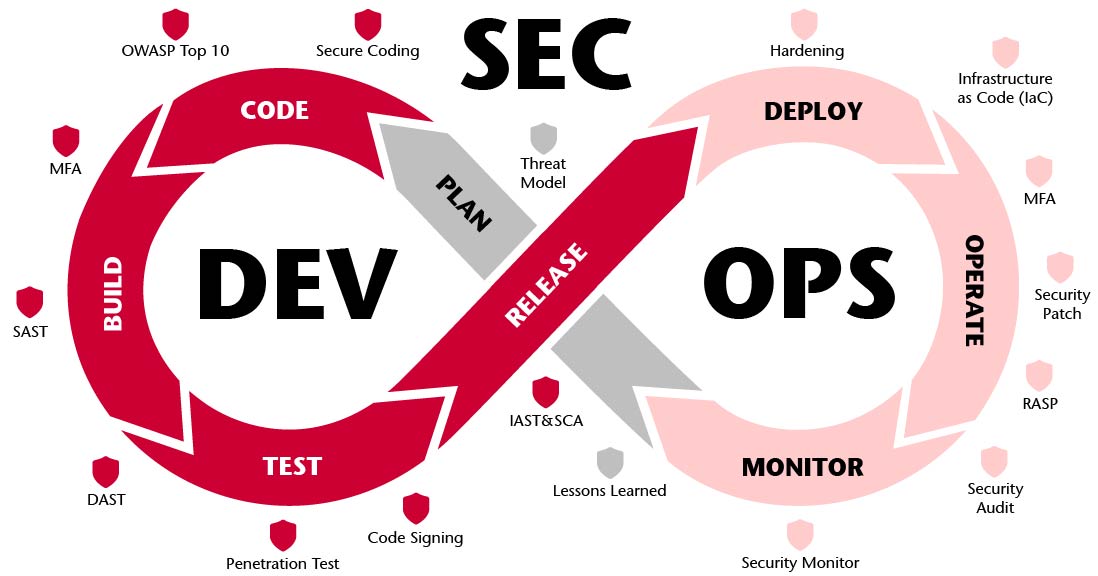
Your bonus
We show you how you can optimise or further develop your existing development and operational processes with regard to an efficient and up-to-date DevSecOps lifecycle.



